A simplified view of the Enigma
Introduction
Rotor Cipher Machine
A type of cipher machine can use several approaches to transform the plaintext into an encrypted message. A common approach is the use of rotors. The Sigaba machine is a typical example of a rotor machine.
A rotor is a device that permutes cryptographic units (usually letters of the alphabet). Each time a rotor turns (hence its name), a new permutation is created. A cipher machine equipped with several rotors can create a very high security cipher.
In another web page, we describe in detail the concept of rotor.
Enigma machines
Enigma machines are special. Indeed, they are equipped with a reflector that greatly complicates the encryption while simplifying its use, because encryption and decryption are identical operations. In a machine like the Sigaba, the electric current passes through several rotors. The current must be reversed to perform the decryption.
In Enigma machines, the current passes through each rotor and then passes through the reflector which returns the current which passes through each rotor again but in the opposite direction. This has two consequences:
- The equivalence between encryption and decryption: if we encrypt the letter A and
obtain the letter E (for example), the encryption of the letter E will give the letter A.
What motivated this choice of the German cryptological service is that it avoids the cipher clerk to make a mistake in the encryption mode (encryption / decryption). Unfortunately this small advantage brings a huge disadvantage (which completely erases the previous advantage): it greatly simplifies the work of the enemy cryptanalyst: encryption and decryption are symmetrical and a letter cannot be encrypted by itself.
- The number of permutations is doubled: instead of having one permutation per rotor, we have two.
Abstract and simplified vision of the Enigma
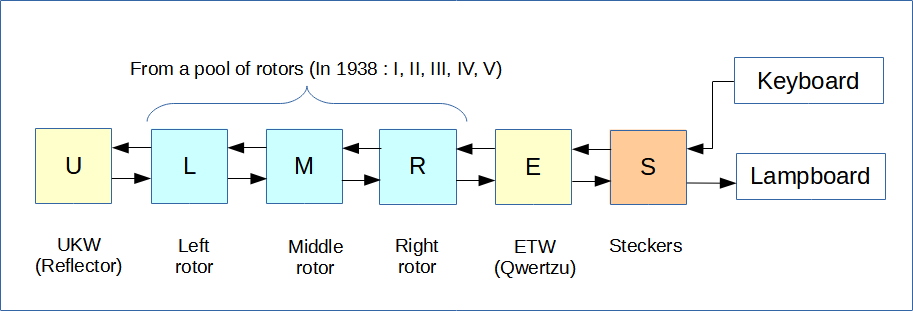 |
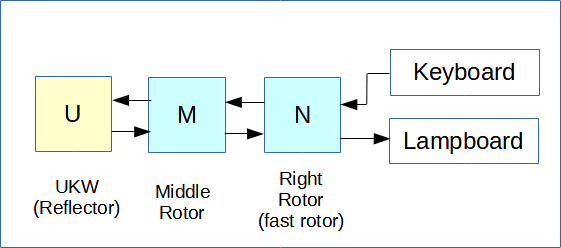
Figure 1 shows the encryption performed by the most common version of the Enigma: The military Enigma 1. It is equipped with a static reflector (U) and then three rotors (L, M, N). The rightmost rotor is called the "fast rotor" because it turns one step before encrypting each letter. The other two rotors turn less frequently. Then a set of cables connects the last rotor to the keyboard. This is the ETW that Dilly Knox nicknamed "QWERTZU". Finally, the steckers allow several letters to be swapped two by two.
The Enigma I is the machine that was broken by Rejewski and against which the Bletchley Park cryptanalysts fought the most.
In fact, there are many other models, for example the commercial Enigma which does not have steckers and whose reflector is not static. The four-rotor Enigma of the German Navy. On the other hand, the British Typex machine can be considered as an Enigma composed of five rotors, two of which do not advance during encryption.
Figure 2 shows our simplified Enigma. Only one rotor will be used in addition to the reflector. The other equipment (ETW, Steckers, ...) will be absent. On the other hand, only six encryption units (0,1,2,3,4,5) will be used, which will replace the 26 letters of traditional Enigmas.
In the following paragraphs, we will study in details our simplified version of the Enigma.
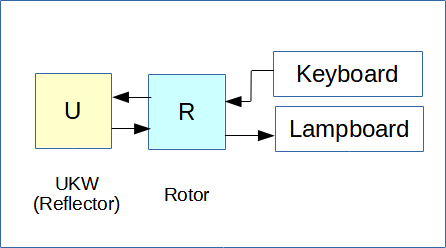 |
Representing our Enigma via drawings
 |
 |
 |
 |
 |
 |
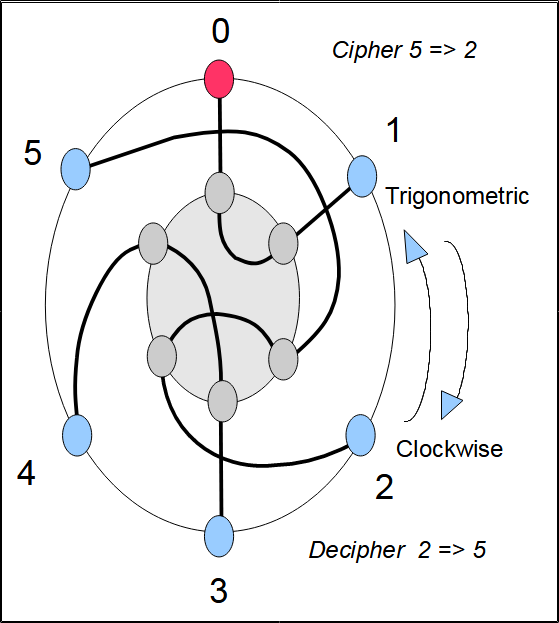
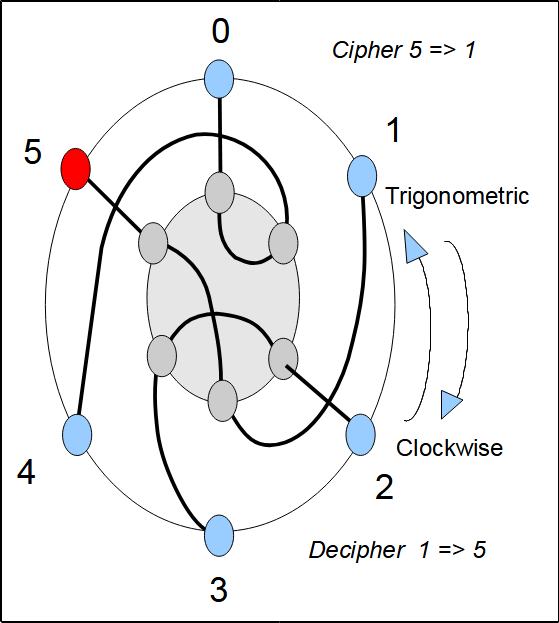
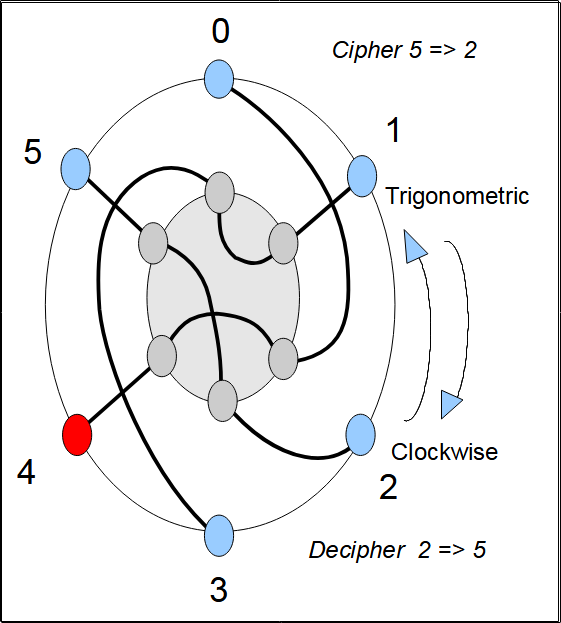
Figures 3 to 8 show the current flow in our simplified Enigma at the different positions of the rotor. The Enigma rotates in a trigonometry direction (counterclockwise). The operator looks at the machine seen perceptively from the right: first seeing the rotor and in the background the reflector. The red dot is attached to the rotor and allows its position to be materialized.
Example of encryption: at position 2 of the rotor, if we encrypt 5 we obtain 2. At the rotor output 5 gives 5, then the reflector transforms the 5 into 3. The rotor crossed in the opposite direction transforms 3 into 2. Since encryption is equivalent to decryption, the encryption of 2 gives 5.
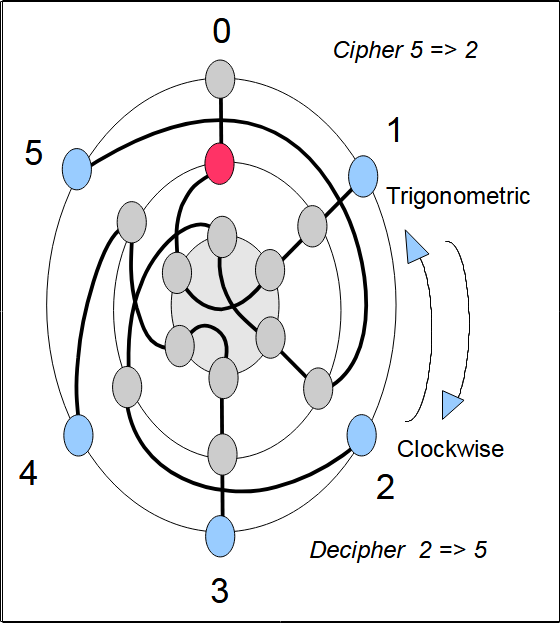
Figure 9 shows the Enigma at various rotor positions, but unlike Figures 3 through 8, the Enigma is viewed from the side.
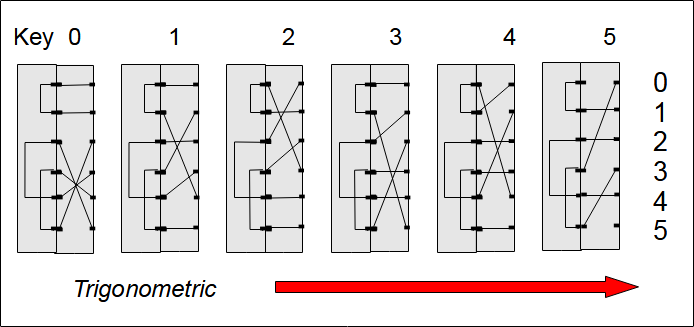 |
Using tables to represent our Enigma
Encryption by the Rotor and the Reverse Rotor
A table is used to represent the encryption of a rotor. The different possible tables have been described in the Rotor page. In our case, the rotor advancement is in the counterclockwise direction (trigonometric direction). In the first table above, the column headers indicate the position of the rotor. The row headers indicate the letter that we want to encrypt (0, 1, 2, 3, 4, 5).
The first column indicates the wiring of the rotor at the initial position (position 0). The diagonals correspond to the wiring of the input disk, the ETW (Qwertzu). If the ETW is absent or if it corresponds to the identity permutation (A=>A, B=> B, C=> C, …, Z=>Z). Here, the diagonals correspond to the sequence 0, 1, 2, 3, 4, 5 (from top to bottom, from right to left).
For example, at rotor position 4, the encryption of 2 gives 2. In the second table, we have the reverse rotor encryption table. This is used in our Enigma at the output of the reflector.
Rotor Reverse Rotor
0 1 2 3 4 5 0 1 2 3 4 5
--------------- ---------------
0 | 0 0 2 0 1 3 0 | 0 0 3 0 4 5
1 | 1 3 1 2 4 1 1 | 1 4 1 5 0 1
2 | 4 2 3 5 2 2 2 | 5 2 0 1 2 2
3 | 3 4 0 3 3 5 3 | 3 1 2 3 3 0
4 | 5 1 4 4 0 4 4 | 2 3 4 4 1 4
5 | 2 5 5 1 5 0 5 | 4 5 5 2 5 3
Encryption performed by our Enigma
In this case, we do not have two tables, but only one, because encryption is equivalent to decryption. As before, the column header indicates the rotor position and the row header specifies the encrypted or decrypted letter. For example, encrypting 5 at rotor position 2 gives 2.
Enigma
0 1 2 3 4 5
---------------
0 | 1 4 4 5 4 3
1 | 0 5 3 4 2 5
2 | 5 3 5 3 1 4
3 | 4 2 1 2 5 0
4 | 3 0 0 1 0 2
5 | 2 1 2 0 3 1
Using Mathematical Permutations to Describe our Enigma
We have the following permutations:
- N = Permutation of the Rotor.
- Q = Permutation of the Reflector.
- P = Permutation of the rotation.
- E = Permutation of our Simplified Enigma.
- I = Identity permutation.
\( N = (0, 1, 4, 3, 5, 2) \)
\( Q = (1, 0, 4, 5, 2, 3) \)
\( P = (1, 2, 3, 4, 5, 0) \)
Here is the formula that describes the permutation performed by our Enigma at position i:
\( E_i = P^{i} \cdot N \cdot P^{-i} \cdot Q \cdot P^{i} \cdot N^{-1}
\cdot P^{-i} \)
Here are the different powers of the rotation:
\( P^1 = P^{-5} = (1, 2, 3, 4, 5, 0) = ((0, 1, 2, 3, 4, 5)) \)
\( P^2 = P^{-4} = (2, 3, 4, 5, 0, 1) \)
\( P^3 = P^{-3} = (3, 4, 5, 0, 1, 2) \)
\( P^4 = P^{-2} = (4, 5, 0, 1, 2, 3) \)
\( P^5 = P^{-1} = (5, 0, 1, 2, 3, 4) \)
\( P^6 = P^{0} = I = (0, 1, 2, 3, 4, 5) \)
For example: \( E_2 = P^{2} \cdot N \cdot P^{-2} \cdot Q \cdot P^{2} \cdot N^{-1} \cdot P^{-2} = ((0 4)(1 3)(2 5)) = (4, 3, 5, 1, 0, 2) \)
Notes:
- For a more complete description of the permutations, see our page on rotors.
- When I use double parentheses ((...)) it is to indicate the use of cycles. When I use simple parentheses, it corresponds to the usual mathematical notation: (4, 3, 5, 1, 0, 2) 0=>4, 1=>3, 2=>5, 3=>1, 4=>0, 5=>2.
Using the Python SymPy library
Python, thanks to the SymPy library, allows you to manipulate permutations.
Note: Our rotors page contains commented examples of using the SymPy library.
As before:
- N corresponds to the Rotor permutation .
- P corresponds to the permutation representing the rotation of the rotor .
- Q corresponds to the reflector permutation .
- Enigma_X corresponds to the Enigma permutation at position X.
>>> from sympy.combinatorics import Permutation >>> N = Permutation([0,1,4,3,5,2]) >>> N.array_form [0, 1, 4, 3, 5, 2] >>> N.full_cyclic_form [[0], [1], [2, 4, 5], [3]] >>> (~N).array_form [0, 1, 5, 3, 2, 4] >>> P = Permutation([1,2,3,4,5,0]) >>> P.full_cyclic_form [[0, 1, 2, 3, 4, 5]] >>> Q = Permutation([1,0,4,5,2,3]) >>> Q.array_form [1, 0, 4, 5, 2, 3] >>> Q.full_cyclic_form [[0, 1], [2, 4], [3, 5]] >>> (P*N*~P) Permutation(5)(1, 3, 4) >>> (P*N*~P).array_form [0, 3, 2, 4, 1, 5] >>> (P*(~N)*(~P)).array_form [0, 4, 2, 1, 3, 5] >>> ((P**2)*N*(P**-2)).array_form [2, 1, 3, 0, 4, 5] >>> Enigma_1 = P * N * ~P * Q * P * ~N * ~P >>> Enigma_1.array_form [4, 5, 3, 2, 0, 1] >>> Enigma_2 = (P**2) * N * (P**-2) * Q * (P**2) * ~N * (P**-2) >>> Enigma_2.array_form [4, 3, 5, 1, 0, 2] >>> Enigma_6 = (P**6) * N * (P**-6) * Q * (P**6) * ~N * (P**-6) >>> Enigma_6.array_form [1, 0, 5, 4, 3, 2] >>> Enigma_6.full_cyclic_form [[0, 1], [2, 5], [3, 4]] >>> Enigma_1.full_cyclic_form [[0, 4], [1, 5], [2, 3]] >>> Enigma_2.full_cyclic_form [[0, 4], [1, 3], [2, 5]]
Using a mathematical formula to describe encryption
For a single rotor, the formulas are given in the rotors page.
For our simplified Enigma, there are several steps:
- We advance the rotor (before encryption): i = i + 1
- We apply the rotor permutation (in the counterclockwise direction): y = N[ x + i ] -i
- We apply the reflector permutationr: y = Q[ y ]
- We apply the inverse rotor permutation: y = N_inv[ y + i ] - i
i = the rotor position x = the plaintext letter y = the ciphertext letter N = the rotor permutation = [ 0, 1, 4, 3, 5, 2] N_inv = the inverse rotor permutation = [0, 1, 5, 3, 2, 4] Q = the reflector permutation = [1, 0, 4, 5, 2, 3]
Note: Using the previous formulas makes it easier to write an Enigma encryption program.
Example: we encrypt the following message with the initial position (i) at -1.
i = 0 1 2 3 4 5 plain = 0 1 1 0 3 2 Crypto= ?
A – encryption of 0 at position -1:
i = -1 + 1 = 0: y = N[0+0] - 0 = N[0] = 0; y = Q[0] = 1; y = N_inv[1+0] -0 = N_inv[1]=1
In short: 0 gives 1.
B – encryption of 1 at position 0:
i = 0 + 1 = 1; y = N[1+1]-1 = N[2]-1 = 4-1=3; y = Q[3] = 5 : y = N_inv[5+1]-1= N_inv[0]-1=0-1=5
In short, 1 gives 5.
C – Encryption of 1 at position 1 :
i = 1 + 1 = 2 ; y = N[1+2]-2 = N[3]-2 = 3-2=1 ; y = Q[1] = 0 ; y = N_inv[0+2]-2= N_inv[2]-2= 5-2=3
In short, 1 gives 3.
D – Encryption of 0 at position 2 :
i = 2 + 1 = 3 ; y = N[0+3]-3 = N[3]-3 = 3-3=0 ; y = Q[0] = 1 ; y = N_inv[1+3]-3 = N_inv[4]-3 = 2-3 = -1 = 5
In short, 0 gives 5.
E – Encryption of 3 at position 3:
i = 3 + 1 = 4; y = N[3+4]-4 = N[1]-4 = 1-4=3; y = Q[3] = 5; y = N_inv[5+4]-4= N_inv[3]-4 = 3-4 = -1 = 5
In short, 3 gives 5.
F – Encryption of 2 at position 4:
i = 4 + 1 = 5; y = N[2+5]-5 = N[1]-5 = 1-5=2; y = Q[2] = 4; y = N_inv[4+5]-5= N_inv[3]-5 = 3-5 = - 2 = 4
In short, 2 gives 4
To summarize:
i = 0 1 2 3 4 5 plain = 0 1 1 0 3 2 Crypto= 1 5 3 5 5 4
The result is correct. We can verify it with the cipher table of our Enigma given above.
A Simplified Enigma with Two Rotors
Introduction
Much of the demonstrations concerning the Enigma can be explained using our simplified Enigma. To be more general, we must use an Enigma equipped with two rotors. It's more complicated than our first version, but this new version is simpler than a real Enigma with three rotors and 26 contacts.
Note: If we stipulate that the right permutation is fixed, our two-rotor Enigma turns into a one-rotor Enigma but with either an upstream Qwertzu or steckers that intervene before the rotation of the first rotor.
Mathematical view
The formula which describes our Simplified Enigma, but with two rotors.
- E = Permutation of the Enigma with the rotor positions at i (for right rotor), and j (for middle rotor).
- N = Permutation of the Rotor at the right position (the fast rotor)
- M = Permutation of the middle rotor
- U = Reflector permutation (which includes the permutation of the left rotor)
- P = Permutation of the rotation.
Drawings
Figure 10 shows the encryption performed by our simplified Enigma with two rotors. These are the N (right) and M (middle) rotors will be used in addition to the reflector. The other equipment (left rotor, ETW, Steckers, ...) will be absent. On the other hand, only six encryption units (0,1,2,3,4,5) will be used, which will replace the 26 letters of traditional Enigmas.
 |
 |
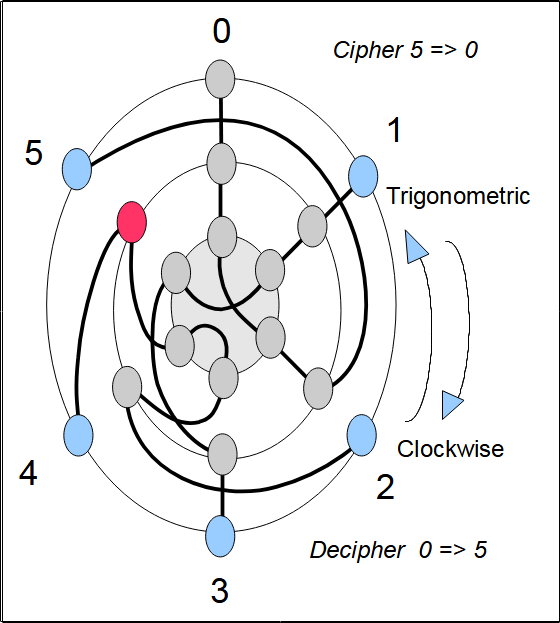 |
Figure 13 shows the Enigma at various rotor positions, but unlike Figures 11 and 12, the Enigma is viewed from the side.
 |
Using Sympy
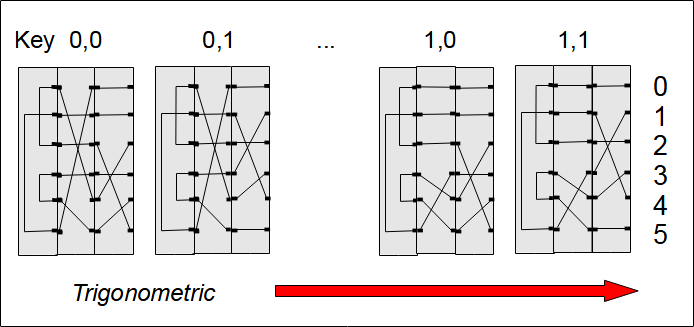
If you want to calculate the permutations shown in the drawings, you can use the following equations in Python with the Sympy library.
>>> >>> P = Permutation([[0,1,2,3,4,5]]) >>> U = Permutation([2,5,0,4,3,1]) >>> N = Permutation([0,1,4,3,5,2]) >>> M = Permutation([5,1,2,3,0,4]) >>> def rot(j,i): ... left = ((P**i)*N*(P**-i))*((P**j)*M*(P**-j)) ... right = ((P**j)*~M*(P**-j))*((P**i)*~N*(P**-i)) ... return left * U * right ... >>> rot(0,0) Permutation(0, 1)(2, 5)(3, 4) >>> rot(0,1) Permutation(0, 4)(1, 5)(2, 3) >>> rot(1,0) Permutation(0, 5)(1, 3)(2, 4) >>> rot(1,1) Permutation(0, 2)(1, 4)(3, 5) >>> rot(2,0) Permutation(0, 3)(1, 4)(2, 5) >>> rot(2,1) Permutation(0, 1)(2, 3)(4, 5) >>>
Cryptanalysis
With the knowledge acquired here, mainly the mathematical vision of the Enigma, we will try to explain several methods of cryptanalysis and first of all the method used by Rejewski at the end of 1932 to find the wiring of the rotors of the Enigma used by the German army.
- The initial breaking of the Enigma by Rejewski
(link)
This initial break allowed to find the wiring of Enigma and first of all, the fast rotor wiring. Rejewski had at his disposal Enigma traffic collected by Polish eavesdropping services and documents from the spy Hans-Thilo Schmidt who worked for the French secret service. - The use of Dilly Knox's Rodding method
(link)
The Rodding method invented by Dilly Knox, allows to find which is the fastest rotor and its initial position. On the other hand, it is necessary to know the wiring of the different rotors which can appear on the extreme right (position of the fast rotor). It is also necessary to have a cryptogram and crib pair. - The use of Dilly Knox's Button-up method
(link)
Dilly Knox found a method to deduce wiring of a rotor from couples of cryptogram and plain text (Crib). His method was effective against the Spanish Enigma but failed against the German Enigma. Dilly did not know the Enigma's "Qwertzu" (ETW). - The breaking of the Commercial Enigma by US Coast Guard
(link)
In 1940, Elizebeth Friedman, who headed the cryptological service of the American Coast Guard, succeeded with her team in reconstructing the wiring of two rotors of the commercial Enigma from several dozen in-depth messages. - The Boxing Method (link)
In 1940, Alan Turing wrote a treatise on the Enigma (the famous Prof's Book). In this book, he described Knox's methods: Rodding and Button-up. He also described the Boxing method, based on the work of Rejewski, for figuring out the rotor wiring of an Enigma. - The breaking of the Commercial Enigma by German
(link)
During the WWII, The german cryptanalysts succeeded in reconstructing the wiring of rotors of a commercial Enigma from several in-depth messages. They used a mathematical approach similar to Turing's.
References
Books & Articles
-
Recovering the military Enigma using permutations—filling in the details
of Rejewski's solution,
by Manuel Vázquez & Paz Jiménez–Seral, Cryptologia, Volume 42, 2018 - Issue 2.
An important preamble is dedicated to permutations allows to master this difficult but essential subject in the understanding of Enigma.